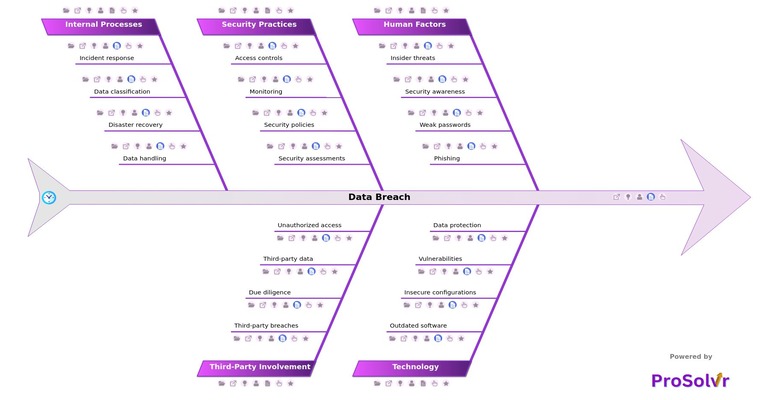
RCA of Data Breach
A data breach occurs when strangers gain unauthorized access to protected, confidential, sensitive, information. This can include personal data, financial records, intellectual property, or other proprietary information. Data breaches can have severe consequences, including financial loss, reputational damage, legal repercussions, and loss of customer trust.
Root Cause Analysis (RCA) of a data breach is a systematic process used to identify the underlying reasons why a data breach occurred. Conducting an RCA helps organizations understand the foundational issues that led to the breach, rather than just addressing the immediate symptoms.
This deep understanding is crucial for implementing effective corrective measures and preventing future incidents. RCA of a data breach help us identify weaknesses in security systems, enhance the incident response plans, highlight the deficiency in employee knowledge, strengthen the compliance and prevent future breaches.
Preventing future breaches through effective RCA can save organizations significant costs associated with breach mitigation, legal fees, regulatory fines, and reputational damage. Identification of the potential causes through RCA and the steps required to address them not only encompasses transparency but rebuilds trust with customers, partners and other stakeholders.
RCA can highlight the need for better security tools and technologies. Organizations might discover that their current tools are insufficient for detecting or preventing certain types of attacks. This insight can drive investment in more advanced security technologies.
Who should use the Data Breach template?
- IT Security Teams: The RCA template facilitates identification of technical vulnerabilities and implements measures to strengthen defenses. This includes patching software, updating systems, and improving network security protocols.
- IT Management: Personnel who oversee IT operations and strategy may gain insights into systemic issues within the IT infrastructure and prioritize investments in security technologies and training programs.
- Risk Management Teams: Managers would find this template useful while mitigating organizational risks. It enables assessing the impact of various vulnerabilities on the organization's overall risk profile and developing risk mitigation strategies.
- Compliance and Legal Teams: Legal teams can ensure compliance with data protection regulations and legal requirements by identifying gaps in compliance and legal safeguards, ensuring adherence to regulations like GDPR, HIPAA, and PCI DSS.
- Senior Management and Executives: It is necessary for senior management to understand the broader implications of data breaches and allocate resources effectively to address root causes and prevent future incidents.
- Operations Teams: Managing day-to-day business operations demands a clear understanding of operational weaknesses that could lead to data breaches and streamline processes to enhance security.
- Internal Audit Teams: Members of this team conduct independent assessments of the organization’s controls and processes. They are responsible for evaluating the effectiveness of current security measures and recommending improvements based on the findings from the RCA fishbone analysis.
- Third-Party Vendors and Partners: They are responsible for providing external services and products that interact with the organization's systems. It is required to understand how their products or services could contribute to security vulnerabilities and improve their own security measures in alignment with the organization’s standards.
- Project Managers: They can manage specific projects within the organization. They need to ensure that new projects incorporate security best practices from the start, minimizing the risk of introducing new vulnerabilities.
Why use this template?
This comprehensive analysis goes beyond addressing symptoms, enabling organizations to implement long-term preventive measures that enhance overall security posture. By clearly categorizing and visualizing potential causes, the RCA template facilitates effective communication among stakeholders, ensures regulatory compliance, and promotes a culture of continuous improvement.
Additionally, it helps prioritize resource allocation, making security efforts more cost-effective and targeted, ultimately reducing the likelihood of future breaches and building trust with customers and partners.
Utilizing RCA tools like ProSolvr and smartQED for data breach analysis significantly enhances the effectiveness of the investigation process. These tools offer collaborative features, structured frameworks, advanced data visualization, AI-powered insights, and comprehensive reporting, all of which contribute to a more thorough and efficient identification of root causes. By leveraging these benefits, organizations can improve their security posture, prevent future breaches, and ensure compliance with regulatory requirements.
Draft and create a template for problem analysis in ProSolvr by smartQED.
Curated from community experience and public sources: